Index
Get the latest news right in your inbox
Identity verification is an indispensable step in order to establish relationships in the economy and in society. This process has traditionally been carried out in a simple way with the face-to-face delivery of identity documentation or the personification in a commercial office as proof of life.
However, the expectations and needs of new consumers have led companies to propose remote models in which both administrative procedures and new registrations and contracts can be carried out over the Internet. Without the person in question in front of the commercial agent who is going to manage this purchase of products or contracting of services, it is a priori easy to commit identity fraud.
As a result, startups have emerged that provide anti-fraud tools to companies wishing to operate online, enabling secure digital ecosystems so that companies and customers can meet on the network and take advantage of all the benefits provided by this means of communication and interaction.
A paradigm shift

Can you imagine taking your car - if you have one - and driving around and around a city looking for properties for sale or rent? This was the reality of the real estate industry decades ago, but now at the click of a button we can find hundreds or thousands of properties in a simple real estate portal. And it is clear to us that no one wants to give this up.
Today's user demands immediacy and 24/7 on-demand services. Operating remotely should be the norm for them, although they clearly continue to demand physical spaces where they can resolve face-to-face queries. The average consumer uses at least two different devices to access the Internet to make purchases or carry out any type of transaction or other commercial operations.
Thanks to the evolution of more secure identity verification technologies, it is now convenient, fast and secure to operate remotely. What's more, frauds such as sim swapping are now more prevalent in physical stores and commercial locations, as many telecommunications companies have these digital identification tools in their online systems. In this way, some have even opted to integrate digital identity verification systems into their physical locations, as they relieve sales agents of the task of collecting and storing identity documentation and other information, as well as carrying out exhaustive anti-fraud checks on them.
Identification vs. authentication: meaning and uses
Identity verification is the process by which a person communicates who he or she is, and provides proof of this, and this information is analyzed to confirm with exhaustive methods that it is true and legitimate. This is done prior to sensitive procedures such as opening a bank account, and signing a contract such as insurance or contracting services. In the online identity verification process, image-based technologies and data interpretation through officialized standards are used to corroborate identity.
The digital identification process generally occurs only once, when the user is registered in the system through the digital onboarding models. With this, the new customer is registered in the organization's database along with his personal data and proof of identification. Once this is done, credentials are generated to prove that it is him without the need to provide so many proofs.
Authentication is the process by which a user proves that he is who he claims to be. In other words, the difference between authentication and identification lies in the provision of evidence and intent. In the online identity verification process, we want to present ourselves to an organization for the first time by communicating who we are, whereas, in authentication, the system already knows us and must confirm that we are the same person who performed the onboarding and identity verification process at the time.
In this way, people access their customer or user accounts to manage their products and services or make use of them. The credentials with which they access can be one or several. In multi-factor authentication strategies, various mechanisms are used to confirm the identity of the person requesting access. There are standards such as SCA (Strong Customer Authentication) that use traits confirmed during the online identity verification process as an authentication factor.
Verifying the digital identity of online subjects
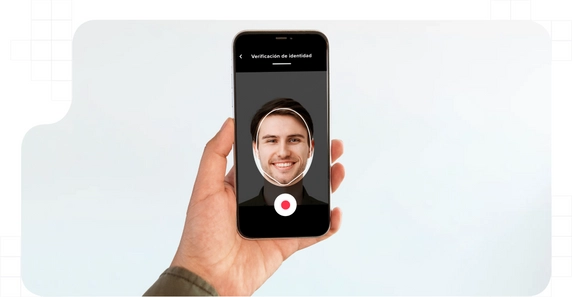
Digital identity verification occurs when two or more parties who are not present in the same physical location wish to conduct a joint operation or transaction remotely. Given the risks faced by individuals and companies when operating over the Internet, such as identity theft and other methods of fraud, it is crucial to have systems in place to ensure that the organization or person we are dealing with remotely is the one we want to deal with.
In addition, beyond security and trust between the parties to proceed to operate, the provision of identity documentation is necessary for certain actions. What systems are companies using to verify the identity of their potential customers and be able to register them?
Customers: Know Your Customer (KYC)
The KYC process is the standard for performing identity checks when initiating a customer onboarding. It is a simple process that consists of a series of steps in which the user provides evidence to confirm that they are who they say they are. This evidence is analyzed by automated systems that can surpass the reliability with which a human performs security checks.
In the procedure, identity documents are analyzed, photographs and videos of the client are taken together with this documentation and technical controls are carried out to check the environment and support from which the client is operating. It is a standardized process that must comply with a series of requirements set out in the law and regulations of the states and institutions that regulate the different industries.
The use of facial biometrics, voice recognition systems, as well as hundreds of environmental and device controls ensure unparalleled security in digital identification processes over the Internet. Operating online is now practically more secure than in person, because in seconds documents that could be falsified are analyzed and the data required to register a customer are collected without the customer having to spend time writing them down character by character.
It is especially important in areas such as FinTech, InsurTech and in general any activity that is likely to involve economic risks. For this reason, there is a term that always accompanies Know Your Customer: the prevention of money laundering. In certain sectors there are dozens of regulations that set standards to prevent this practice and companies must use KYC systems to meet their AML obligations in onboarding processes.
Companies: Know Your Business (KYB)

B2B businesses deal with other companies on a daily basis. Moreover, in recent years dozens of innovative business models have emerged that base the core of their activity on interaction with other companies and incorporate hundreds of businesses into their system every day.
Given this, the need has arisen to incorporate Know Your Business platforms to ensure the smooth running of your business. The controls are similar to those of KYC but this time business documentation and other sensitive information is analyzed. Due diligence checks can also be added for additional security.
The best dynamic OCR technologies make it possible to identify digital identities and validate complex documentation in seconds thanks to technological advances in artificial intelligence and machine learning. Even in a dynamic way and without the need to previously select the document to be validated, digital identification platforms.
The best digital identity verification systems

Digital identification has evolved by leaps and bounds in recent years. SaaS systems have allowed businesses to incorporate these tools into their structure in days with total simplicity and an adjusted price. Unlike costly ad-hoc platform developments by large consulting firms, RegTech startups are now accompanying leading companies in all sectors of activity as Trust Services Provider to guarantee their activity.
Previously, these costly developments involved projects lasting months or even years, which, moreover, became obsolete in a short period of time. Now, digital identification is carried out on cloud platforms that are perfectly integrated through APIs in the channels, websites and applications of companies without the user noticing.
In addition, these platforms provide an enhanced experience due to their polished interfaces. Thanks to specialization, knowledge of the flow of steps in these processes results in speed and agility, something that guarantees conversion.
Many trusted service providers have also been able to incorporate electronic signature solutions into their digital identity verification systems for online contracting in the same process. In this way, we do not have two applications, one to identify customers digitally and another to sign the contract or buy the product. In the same gateway, both processes are performed simultaneously and organically.
























