Index
Get the latest news right in your inbox
SIM Swapping has increasingly proven to be one of the main challenges faced by companies in the telecommunications sector.
In the telco industry, due to the nature of its activity, there are very delicate cases that require specific tools that can be agile and comfortable for both the user and the commercial agents without sacrificing security.
After an era of much less stringent controls, the processes for issuing, duplicating and activating SIM cards were completely transformed. In many countries, following severe criminal events, the technical and regulatory standards for how these processes should be carried out were tightened, but criminals nevertheless found ways to circumvent some systems.
With the advent and spread of digital services and products and, later, the implementation of multi-factor authentication controls, SIM swapping saw the opportunity to take advantage of certain circumstances.
SIM Swapping. What does it involve?
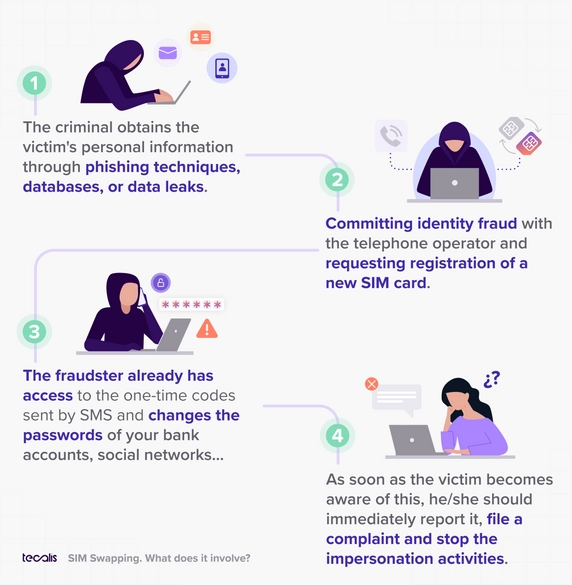
SIM Swapping is a method of identity theft using a SIM card that legitimately belongs to someone else and is now in the hands of a criminal. This type of fraud makes sense, especially in an environment where multi-factor authentication is the method of access to sensitive platforms and where a user can perform very important transactions.
Also known as "SIM spoofing" or "SIM duplication/duplication", SIM swapping is much more widespread than it might seem and, in 2022, multi-million dollar penalties have been imposed on telephone operators for not having the appropriate tools to manage their customers' data securely and prevent this type of criminal threat.
In this fraud, the offender makes a duplicate SIM card of a phone pretending to be the legitimate owner of that number. Thus, the first step, and the decisive one for a criminal to carry out this process, is the impersonation of a person of whom he already has some information such as his email and name.
And it is much simpler than it might seem, since, today, these data are public and those that allow us to operate both in the network and at a personal and professional level. The problem arises when telecommunications companies do not use exhaustive methods to identify users who request a duplicate SIM card.
Once the criminal has gained access to the phone number, he uses it to obtain the one-time codes that are sent via SMS by multi-factor authentication systems with only non-biometric factors to access, for example, the victim's digital online banking tools, impersonating the victim and being able to operate on his behalf.
Therefore, and given the penalties that have occurred in the telecom sector for not properly addressing this threat, SIM Swapping is currently one of the main issues to be resolved by telcos and sales channels.
Mandatory identification requesting a SIM card
In order to issue, duplicate and activate SIM cards, both prepaid and when contracting new flat-rate services, it is necessary for the person to identify himself/herself properly. The identification process requires simply providing a copy of the ID card, which is stored in the telecommunications company's system.
The importance of processes at the point of sale

One of the most decisive challenges faced by telephone companies is undoubtedly the management of their sales channels. The capillarity of their networks often leads to a lack of attention to detail in certain procedures.
Currently, many sales channels simply store the person's identity document, without carrying out additional checks to verify that the person providing the document is who he or she claims to be and that it is legitimate and not forged. It is even the case that a person can authorize another person through a simple document, signed in any way, to register a SIM card in his name.
Thus, in SIM duplication, companies in the telecom sector must resolve two major challenges, which are penalized by the casuistry of this procedure:
- Compliance with data protection and privacy regulations (RGPD and others).
In most sales channels these anti-fraud controls are carried out by the employee himself, who, on behalf of the company, is responsible for both certifying that the process is being carried out in a safe and secure environment and that the data will be processed on the company's systems in accordance with the required data protection laws and security requirements.
Telco sales channels are roughly divided into own stores, call centers, web pages, commercial stands and the alternative channel. SIM duplication and activation processes can be carried out in all of them, especially in the face-to-face ones. To resolve certain aspects, companies usually choose to define certain guidelines and different ways of proceeding depending on the type of channel.
This might seem to solve some of the problems related to SIM Swapping, but it has the opposite effect. Commercial agents in the different channels do not always have the same information or the same tools to perform certain processes, resulting in inefficiencies and, sometimes, failures in meeting the two major challenges mentioned above.
Therefore, the company is delegating responsibility to these commercials, although, at the end of the day, it is ultimately responsible for what happened in these processes.
Digital tools to combat SIM Swapping
The development of innovative software and digital platforms has been a game-changer for the most important use cases in all industries.
The telecommunications sector, a benchmark in terms of innovation in technology, has been able to take advantage of the solutions offered by expert partners in these areas to incorporate tools in their systems that, on the one hand, eliminate any type of risk and problems in their daily activity and operations and, on the other hand, boost their activity by being able to expand their product and service offerings by deploying their network with total confidence without impacting their IT teams.
These digital platforms are able not only to manage the processes of issuing, duplication and activation of SIM cards in an agile and automated way but also to prevent any attempt of SIM Swapping, among many other crucial and daily use cases of companies in the telecom sector.
In either case, and regardless of whether they are performed in any type of proprietary or alternative channel, the responsibility would then fall on the identity verification system provided by a third party, and not on the telecommunications company or its commercial agent or alternative channel partner.
These systems make use of tools already used in polished and tested digital onboarding processes with exhaustive controls seen in other sensitive industries such as finance, banking, insurance and related industries.
First, a series of customer data is collected depending on the sales channel, but always with the same platform, and then the identity is verified with techniques of the already known KYC (Know Your Customer) that are adjusted to be applied in the telecom sector operations adapted to their specific needs and circumstances. This is done in an agile way and in seconds thanks to its design.
In an operating model that relies on such solutions facilitated by a holistic digital platform and seamlessly integrated into the company's own systems, a double benefit is obtained:
- The telcos are confident that they will not be fined by the institutions because a third party performs the procedure for them securely and in accordance with the highest technical and regulatory standards,
- and users can rest assured that they will never fall victim to SIM swapping fraud due to the absolute reliability of these expert and specialized systems.
The best SIM Swapping tools are those that are part of a comprehensive solution for managing processes in the sales channel, as they ensure that the supplier is an expert in the telecom sector. Likewise, the system must have biometric-based authentication methods such as facial recognition.
These types of factors are incapable of being falsified or used by infringers. In addition, their speed, versatility and legal backing make it possible to close processes that take days to minutes, one of the aspects most criticized by clients and users in the telecommunications sector.
Consequences of SIM Swapping for customers
Beyond the obvious consequences of being a victim of fraud, SIM Swapping has impacted the experience users have when interacting with their telecommunications company.
The response of many operators has been to increasingly limit the ways to perform a duplicate SIM, portability or any related process in which a customer must be properly identified. This is resulting in the loss of customers and commercial opportunities for the companies.
Holistic digital platforms with solutions to tackle SIM Swapping are not only able to prevent this fraud but also help companies to design a polished, agile and secure customer journey that is designed with the user experience in mind so that the user finds what they are looking for when interacting with a telco:
- Agility in the processes, without frictions that cause abandonment due to idleness.
- Sense of security and guarantees.
- Differential product and service offers are available in any of your operator's channels.
- Positive perception of the brand in sales and communication channels.
The business model of companies in the telecom sector

Investing time and resources in developing advanced technology can lead companies to inefficient models. Experience has shown that SaaS solutions from experienced technology providers have revolutionized the telecommunications industry.
Companies operate in diverse and highly competitive markets in which the ability to respond immediately is a differential point for growth and sustainability. This ability to respond to the needs and demands of customers and the business is no longer an option, it is a necessity.
Thus, the way to position itself as a leader in the sector today is to rely on dedicated, committed but agile teams, without external supplier rotation, to develop solutions based on proven technologies that can be integrated into the structure of the business in a matter of weeks.
This has reduced the time-to-market in deployments of new offerings in a way never seen before, in addition to the fact that these solutions adapt to each phase of the business cycle and ensure their future scalability under a pay-per-use model.
100% unattended and secure Auto-SIM processes

If we were to highlight an application of the tools for dealing with SIM Swapping that not only have this function as their sole objective, we would highlight the Auto-SIM procedures.
This application occurs in use cases of any kind, from a tourist who wants to activate a SIM to portability processes, and runs as follows:
- The customer purchases or receives his SIM card.
- Scan a QR code or access a URL.
- Basic customer data that the operator deems necessary is requested.
- It asks for the number, the ICCID of the old card if it is portability or duplicate, and that of the new one, and may ask for several additional authentication factors to be entered. In the case of a postpaid card, for example, the last 4 digits of the bank account may be requested.
- An automated identity verification process is carried out by video identification streaming in real-time that verifies the legitimacy of the identity document and the data previously provided more efficiently than a human agent and crosses that information with a video where the user performs an action (move the head, smile...) to verify that he is who he claims to be under the most demanding legal and technical standards.
- If point 4 was performed correctly, calls are made to the systems to activate the services.
In a semi-served process, the agent would perform the first four steps on their work platform and assist the customer by helping them perform the fifth step. However, the best solutions are able to guide the user autonomously through a digital platform with conversion rates above 98%. Likewise, the platforms adapt these processes to be perfect for each type of commercial channel (call, store, online...).
In either case, the ultimate responsibility for problems related to SIM Swapping would lie with the user identified if he/she is trying to commit an infringement, and the system would detect it instantly, and with the application and the application provider, who are the ones who approve and certify the process.
























